OTP Explained: The Ultimate Guide to One-Time Password

Intro to OTP Technology
In an era where cybersecurity threats are evolving rapidly, ensuring secure and user-friendly authentication has become a top priority for organizations. Traditional passwords, despite being a long-standing method, are increasingly vulnerable to hacking and unauthorized access. One effective solution that has gained widespread adoption is the use of One-Time Passwords (OTPs).
This article delves into OTPs, their types, working mechanisms, benefits, drawbacks, and real-world applications.
What is an OTP?
A One-Time Password (OTP) is a unique, dynamically generated code used for verifying a user’s identity during login or transaction approvals. Unlike traditional passwords, OTPs can only be used once and expire after a short duration, reducing the risk of unauthorized access.
Thanks to their high security and ease of use, OTPs are often integrated into Multi-Factor Authentication (MFA) systems to provide an additional layer of protection.
Types of OTPs
There are two primary types of OTPs, each utilizing different mechanisms:
1. Hash-Based OTP (HOTP)
HOTP follows the HMAC-based One-Time Password (HOTP) standard, documented in RFC 4226. It uses a counter that increments every time a new OTP is generated. The same counter value is maintained on both the client device and the authentication server to validate the OTP.
Pros:
- Does not expire immediately, allowing users more time to input the code.
- Suitable for offline authentication scenarios.
Cons:
- More susceptible to brute-force attacks due to a longer validity period.
- Requires synchronization between the client and the server.
2. Time-Based OTP (TOTP)
TOTP, defined in RFC 6238, generates OTPs based on the current timestamp. The code refreshes after a fixed time interval, typically between 30 and 90 seconds.
Pros:
- Provides stronger security due to its time-sensitive nature.
- Reduces the risk of OTP reuse or replay attacks.
Cons:
- Requires precise time synchronization between the client and server.
- Users must enter the OTP quickly before expiration.
How OTPs Are Delivered
OTPs can be sent via multiple channels, each offering different levels of security and convenience:
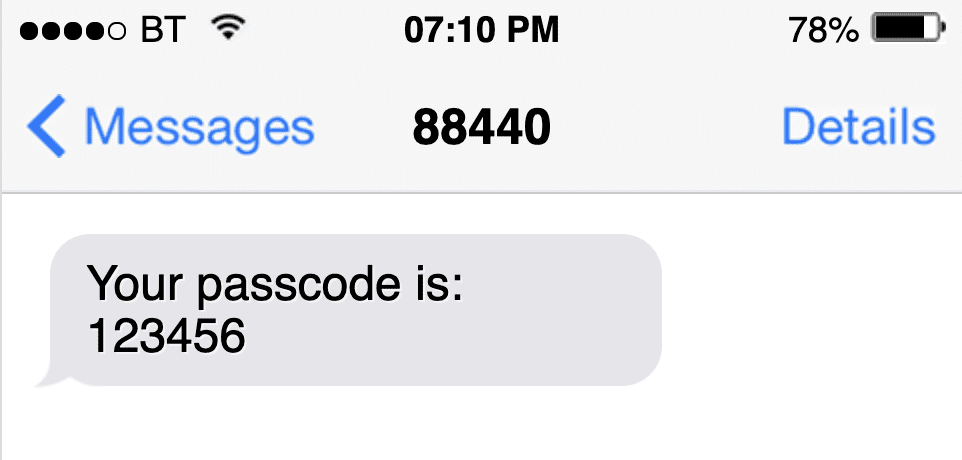
- SMS OTP: Sent as a text message to the user’s mobile number. While widely used, SMS-based OTPs are vulnerable to SIM swapping and interception.
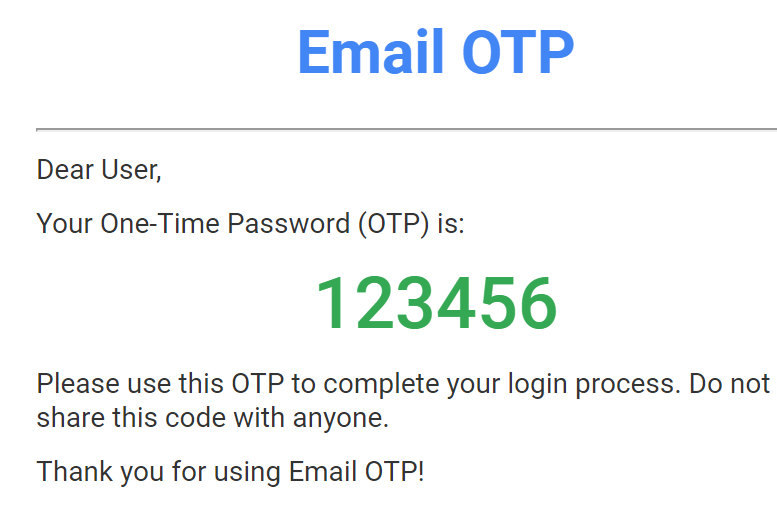
- Email OTP: Delivered to the user’s registered email address. It provides an alternative to SMS but is reliant on email security.
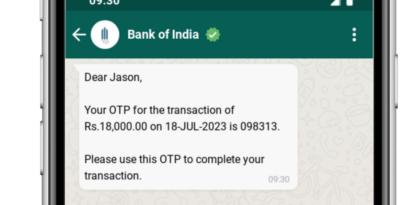
- Messaging Apps (WhatsApp, Telegram, WeChat): Encrypted messaging platforms offer a secure way to receive OTPs, reducing the risk of interception.
- Hardware Tokens (YubiKey, RSA SecurID): Dedicated devices generate OTPs without relying on mobile networks or the internet, making them highly secure.
- Authenticator Apps (Google Authenticator, Microsoft Authenticator, Authy): These mobile applications generate time-based OTPs offline, reducing exposure to cyber threats.
Benefits of OTPs
- Enhanced Security: OTPs mitigate risks associated with stolen passwords and brute-force attacks.
- Protection Against Replay Attacks: OTPs expire after a short period, preventing their reuse.
- User Convenience: Users do not need to remember complex passwords; they receive new OTPs on demand.
- Seamless Integration: OTPs can be incorporated into existing authentication systems without major infrastructure changes.
Challenges and Limitations
- Dependence on Delivery Reliability: SMS and email OTPs may face delivery delays or failures.
- Phishing Risks: Attackers can trick users into revealing OTPs through social engineering tactics.
- Server Vulnerability: Since OTP generation relies on shared secrets, if compromised, an attacker could generate valid OTPs.
Real-World Use Cases of OTPs
1. Financial Services & Banking
Banks use OTPs for secure online banking, fund transfers, and transaction verification, preventing unauthorized access and fraud.
2. Healthcare
Hospitals and healthcare providers use OTP authentication to secure patient records and comply with HIPAA regulations.
3. E-commerce
Online retailers employ OTPs for secure login and checkout processes, ensuring that only authorized users can complete high-value transactions.
4. Government Services
Government agencies implement OTP authentication for digital services like tax filing, voting, and citizen portals to enhance security.
5. IT & Cloud Services
Technology firms use OTP authentication to secure cloud access, administrative accounts, and software-as-a-service (SaaS) platforms.
Enhancing Security with OTP Authentication Providers
Adding OTP authentication to applications can be time-consuming for developers. However, platforms like Descope provide no-code workflows, SDKs, and APIs to simplify OTP integration. These solutions help developers implement OTP authentication quickly and efficiently while ensuring robust security measures.
Final Thoughts
OTPs have revolutionized authentication by offering a secure, user-friendly alternative to traditional passwords. While not without challenges, OTPs significantly enhance security and are widely adopted across industries. Organizations looking to strengthen their authentication processes should consider integrating OTPs into their security framework, leveraging modern authentication providers for seamless implementation.
By implementing OTPs strategically, businesses can enhance security, streamline user experiences, and stay ahead of cyber threats in an increasingly digital world.
Read more🌐 about latest Tech updates on out Technology Category Section
#CyberSecurity #OTP #MFA #Authentication #TechSecurity #OnlineSafety #2FA





