Understanding Single Sign-On (SSO): A Comprehensive Guide

Intro to Single Sign-On
In today’s digital landscape, where multiple platforms and applications are integral to business operations, managing user access efficiently and securely is a top priority. Single Sign-On (SSO) technology provides a streamlined solution, allowing users to access multiple applications with just one set of credentials. While SSO enhances user convenience, its implementation is underpinned by intricate security protocols and identity verification mechanisms.
What is SSO?
Single Sign-On (SSO) is an authentication mechanism that enables users to log in once and gain access to multiple connected applications and services. Instead of remembering separate credentials for each service, users authenticate once, and their identity is carried over to other applications within the SSO framework.
SSO benefits both users and organizations by simplifying login experiences, reducing password fatigue, and improving security. Users can initiate an SSO session either through an application (SP-initiated SSO) or by logging into an SSO provider’s portal (IdP-initiated SSO).
SSO vs. Other Authentication Methods
SSO is often compared with other authentication techniques like password managers, Multi-Factor Authentication (MFA), and federated authentication:
- SSO vs. Password Managers: While password managers store multiple credentials securely, SSO eliminates the need for multiple passwords altogether by providing centralized authentication.
- SSO vs. MFA: SSO focuses on reducing authentication steps, while MFA enhances security by requiring multiple authentication factors (e.g., biometrics, OTPs) alongside SSO.
- SSO vs. Federated Authentication: Federated authentication allows users to access services across different organizations, whereas SSO is primarily designed for seamless access within a single organization or platform.
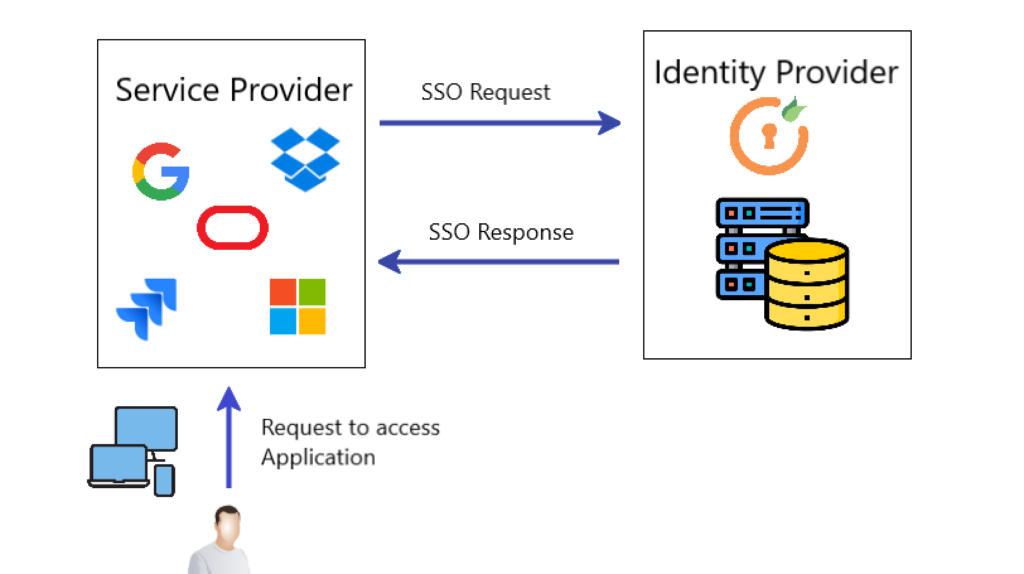
How SSO Works
SSO functions by maintaining a central authentication system that verifies a user’s identity and generates an authentication token. This token is passed between services to grant access without requiring additional logins. The process typically follows these steps:
- User Authentication: The user attempts to log into an SSO-enabled service and is redirected to the SSO provider’s authentication portal.
- Credential Verification: The SSO provider verifies the user’s credentials against its identity repository.
- Token Generation: Upon successful authentication, a token is generated and stored in the user’s browser or session.
- Token Validation: When accessing another service within the SSO network, the stored token is presented, and the service verifies it with the SSO provider.
- Session Continuation: As long as the session remains active, the user can access multiple services without re-entering credentials.
- Session Expiry: When the session ends or the user logs out, the token is invalidated, requiring re-authentication for future access.
SSO Protocols and Standards
SSO operates on various protocols, each catering to different authentication needs:
- SAML (Security Assertion Markup Language): A widely-used XML-based protocol ideal for enterprise authentication.
- OAuth 2.0: Primarily designed for authorization, OAuth enables third-party applications to access user data securely.
- OIDC (OpenID Connect): Built on OAuth 2.0, OIDC facilitates user authentication, particularly in mobile and web applications.
- ADFS (Active Directory Federation Services): A Microsoft-based SSO solution commonly used in corporate environments.
Each protocol has its unique benefits, making it essential to choose one that aligns with an organization’s security and operational requirements.
Benefits of SSO
Implementing SSO offers significant advantages:
- Enhanced Security: Reduces password-related vulnerabilities by limiting the number of credentials users manage.
- Improved User Experience: Eliminates the need for multiple logins, providing seamless access across platforms.
- Centralized Identity Management: Simplifies user access control and monitoring, improving security oversight.
- Increased Productivity: Reduces login-related disruptions, allowing employees to focus on their tasks.
- Regulatory Compliance: Helps organizations meet security and data privacy standards like GDPR and HIPAA.
- Scalability: Easily integrates with enterprise systems, supporting workforce expansion.
Potential Risks and Challenges
Despite its benefits, SSO presents some security and operational challenges:
- Single Point of Failure: If an attacker compromises SSO credentials, they can access all associated services.
- Reliance on SSO Provider: Service downtime or a security breach in the provider can disrupt access across applications.
- Implementation Complexity: Integrating SSO with existing infrastructure requires technical expertise and robust security policies.
Common Use Cases of SSO
SSO is widely implemented across industries to enhance security and streamline authentication processes:
- Enterprises: Used for internal applications, email services, and cloud platforms.
- Healthcare: Ensures HIPAA-compliant access to medical records and patient portals.
- Education: Provides students and faculty with seamless access to learning resources and administration systems.
- E-commerce: Enhances user experience by enabling frictionless login across multiple shopping platforms.
- Government Services: Secures access to citizen portals, tax filing systems, and official databases.
Key Considerations for Implementing SSO
When integrating SSO, organizations should evaluate the following factors:
- Compatibility: Ensure the SSO solution integrates with existing applications and IT infrastructure.
- Scalability: The solution should accommodate growing user bases without compromising performance.
- Security Measures: Implement MFA alongside SSO to strengthen authentication security.
- Vendor Reliability: Choose a trusted provider with robust security measures and continuous support.
Implementing SSO with Ease
While SSO implementation can be technically demanding, platforms like Descope simplify the process with no-code workflows, SDKs, and APIs. These tools help businesses integrate secure authentication seamlessly while focusing on their core operations.
Conclusion
Single Sign-On (SSO) is a game-changer for both security and user experience, enabling centralized authentication across multiple services. While it offers numerous advantages, organizations must assess risks, choose the right protocols, and implement additional security measures like MFA to ensure a robust authentication framework. By leveraging modern identity management solutions, businesses can strike the perfect balance between security and convenience in today’s digital ecosystem.
Read more🌐 about latest Tech updates on out Technology Category Section
#SSO #CyberSecurity #Authentication #MFA #IdentityManagement #TechSecurity #BusinessIT





